Computational Governance🔗
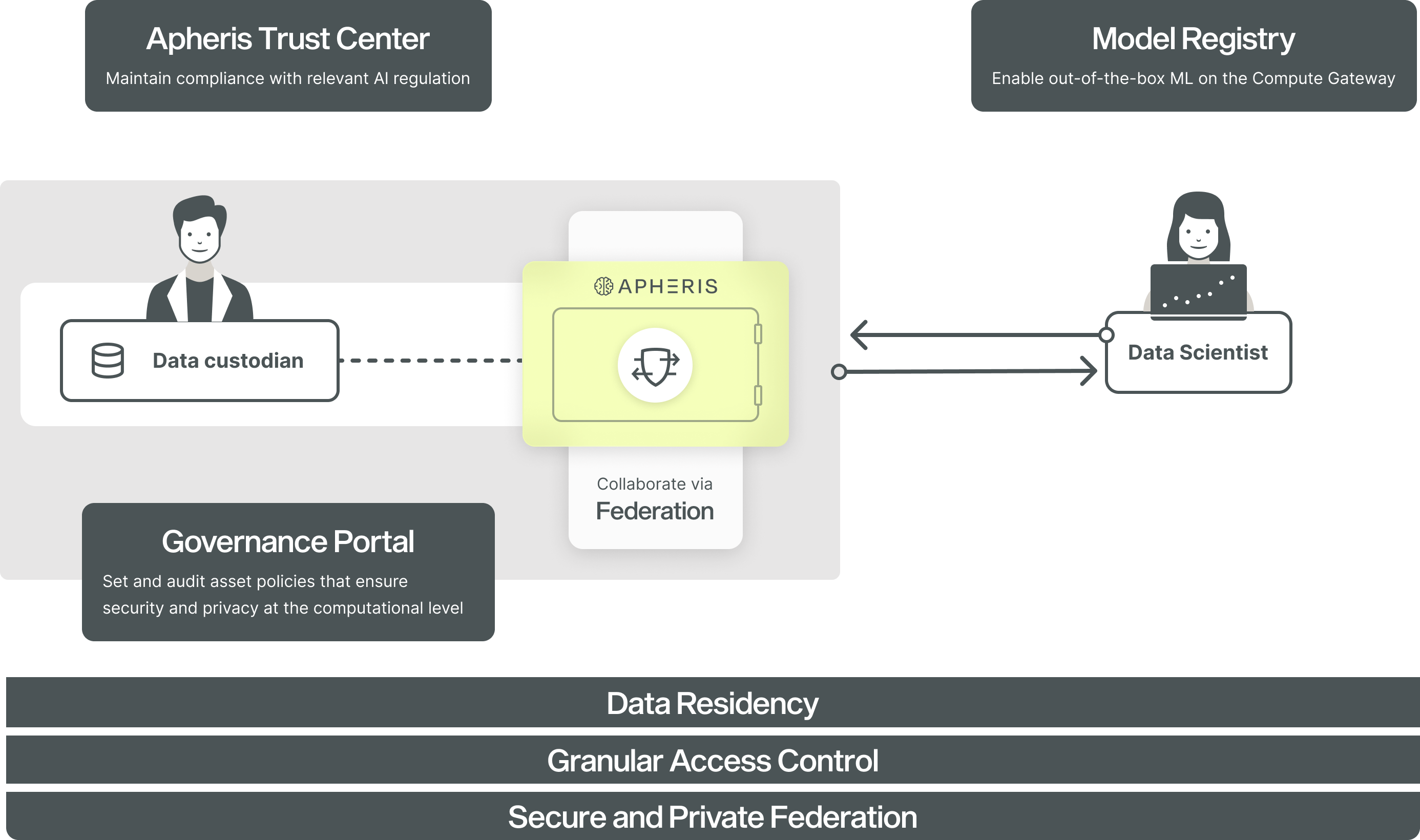
Computational Governance is a key capability of the Apheris Product. It is achieved via the three conceptional pillars
- Data Residency,
- Granular Access Controls,
- and Secure and Private Federation
which together enable secure, private and compliant computations on any data.
Computational Governance is a method to control, supervise, and track all aspects of computations. It works by automatically evaluating incoming compute requests, enforcing privacy and security parameters and overseeing the release of results. This allows data custodians to contribute any data safely to collaborations while preserving data privacy.
Within Apheris, this approach is combined with federated learning methods. This eradicates the need to move data, as computations are sent to the data and get executed within the data custodians environment. Only results aggregates or weights are returned.
How Computational Governance works🔗
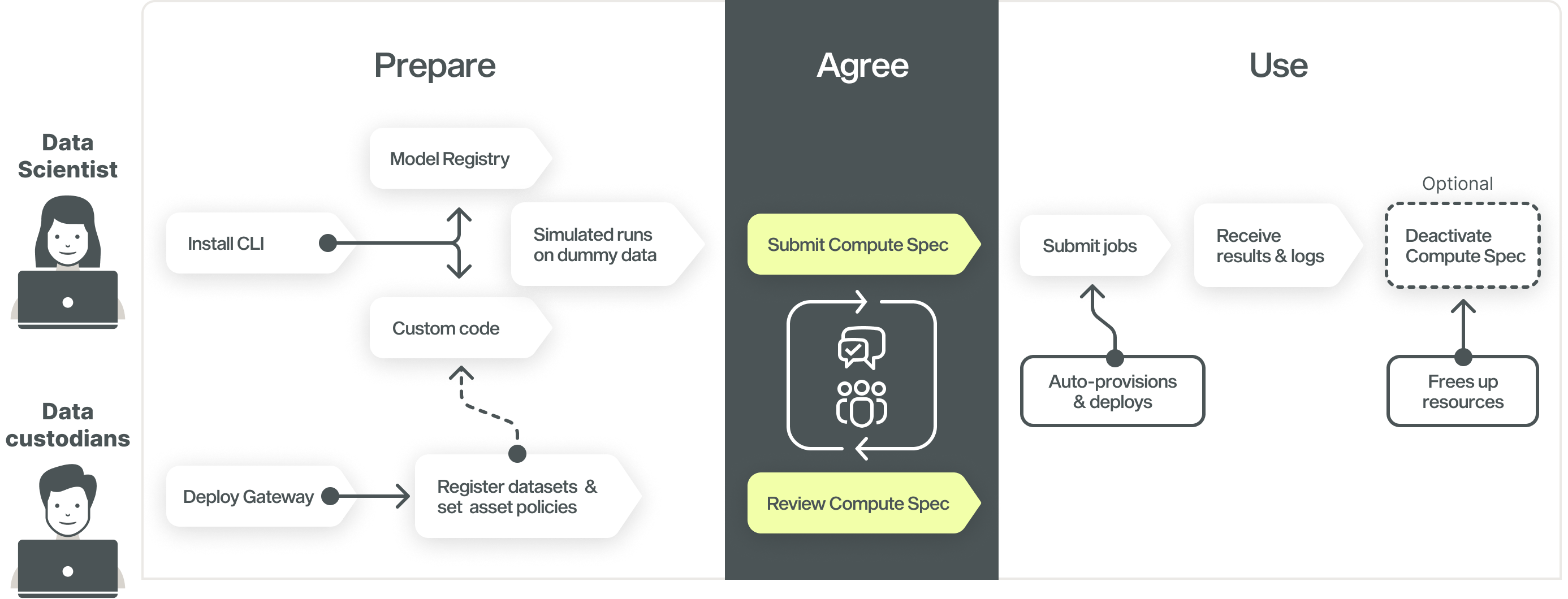
As data-driven analytics use cases can pose different requirements, Apheris strives to provide a simple, yet highly adaptive framework for data custodians and Data Scientists alike.
Computational Governance allows a Data Custodian to define:
- who can send computations;
- which datasets can they run computations on;
- which computations can they run.
The above can be defined and configured with asset policies
Within asset policies, you can select the models from the Model Registry you want to allow. Furthermore, you can set bounds on the runtime parameters/hyperparameters the model is allowed to use. For example you can specify bounds on:
- Number of training runs (epochs);
- Batch size (Number of training examples within one training round);
- Enforced Privacy Controls;
- Permitted statistical functions (Apheris Stats package only).
A Data Scientist can specify a computation which, to be executed on the data, needs to adhere to requirements set out within an Asset Policy. Together, Asset Policies and Compute Specs form a computational agreement.
The Apheris Compute Gateway ensures that only computations operating within the limitations of this agreement can be executed by automatically validating incoming compute requests against the set Asset Policies.
In addition, logs are created for all computations for traceability and auditability purposes.
Scalability of Computational Governance🔗
The Computational Governance methods scales with your use case.
Computational Governance can be applied to any data type, analytical use case and to an arbitrary amount of simultaneous computations by any number of data consumers.
This provides the infrastructure and capabilities to enable data-driven collaborations across various regulatory jurisdictions and organizational boundaries.