Asset Policy overview🔗
Asset Policies are a key feature within Apheris. They are essentially a set of rules that define allowed operations by named users on specified datasets. More specifically, Asset Policies define:
- who can perform computations on which dataset;
- which computations are allowed;
- parameter boundaries for these computations;
- the type of privacy controls to add at runtime (optional).
Below, you will find the most relevant details for each of the four sections of an Asset Policy and possible configurations. If you want to learn how to create an Asset Policy, please see Setting up my first Asset Policy.
You can create an arbitrary amount of Asset Policies for the same dataset. This allows to meet requirements of different use cases and purpose-based permission configuration needed for regulatory compliance.
Please note: Only users with the role “Owner” can create, edit or delete Asset Policies.
The five sections of an Asset Policy🔗
You can add an Asset Policy by navigating to the ‘Asset Policies’ page and clicking on ‘Add Asset Policy’:
Each asset policy has five sections:
- Details: Enter a name and description of the Asset Policy;
- Datasets: Select the datasets the Asset Policy should govern;
- Beneficiaries: State users allowed to run computations;
- Permissions: Select a model and define permissions and privacy controls for the selected model;
- Signature: Sign an Asset Policy (optional).
Beneficiaries🔗
Beneficiaries are users of either your own or an external organization to whom you can grant permission to run computations on a given dataset. Beneficiaries are defined by a user’s full email address.
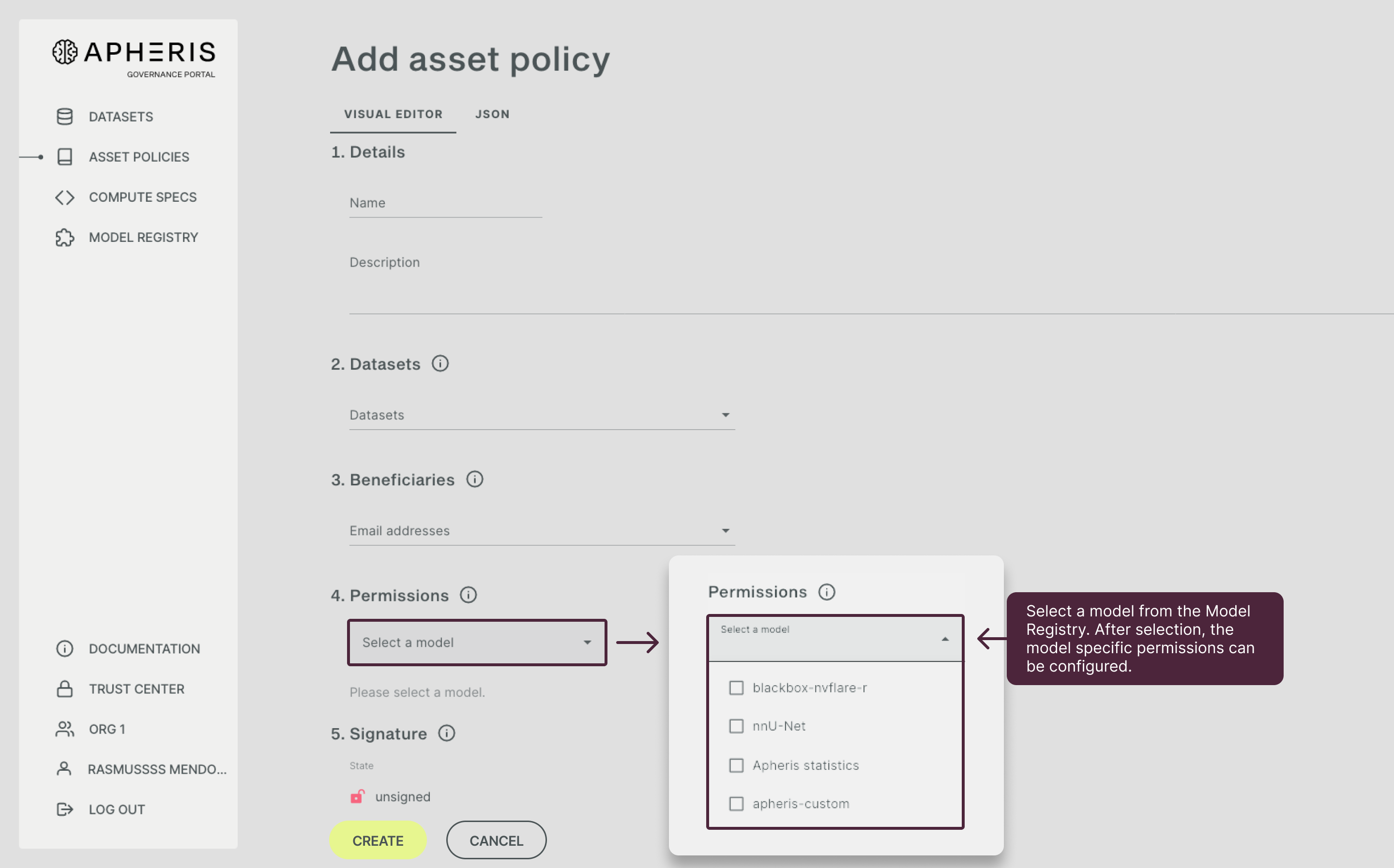
Permissions🔗
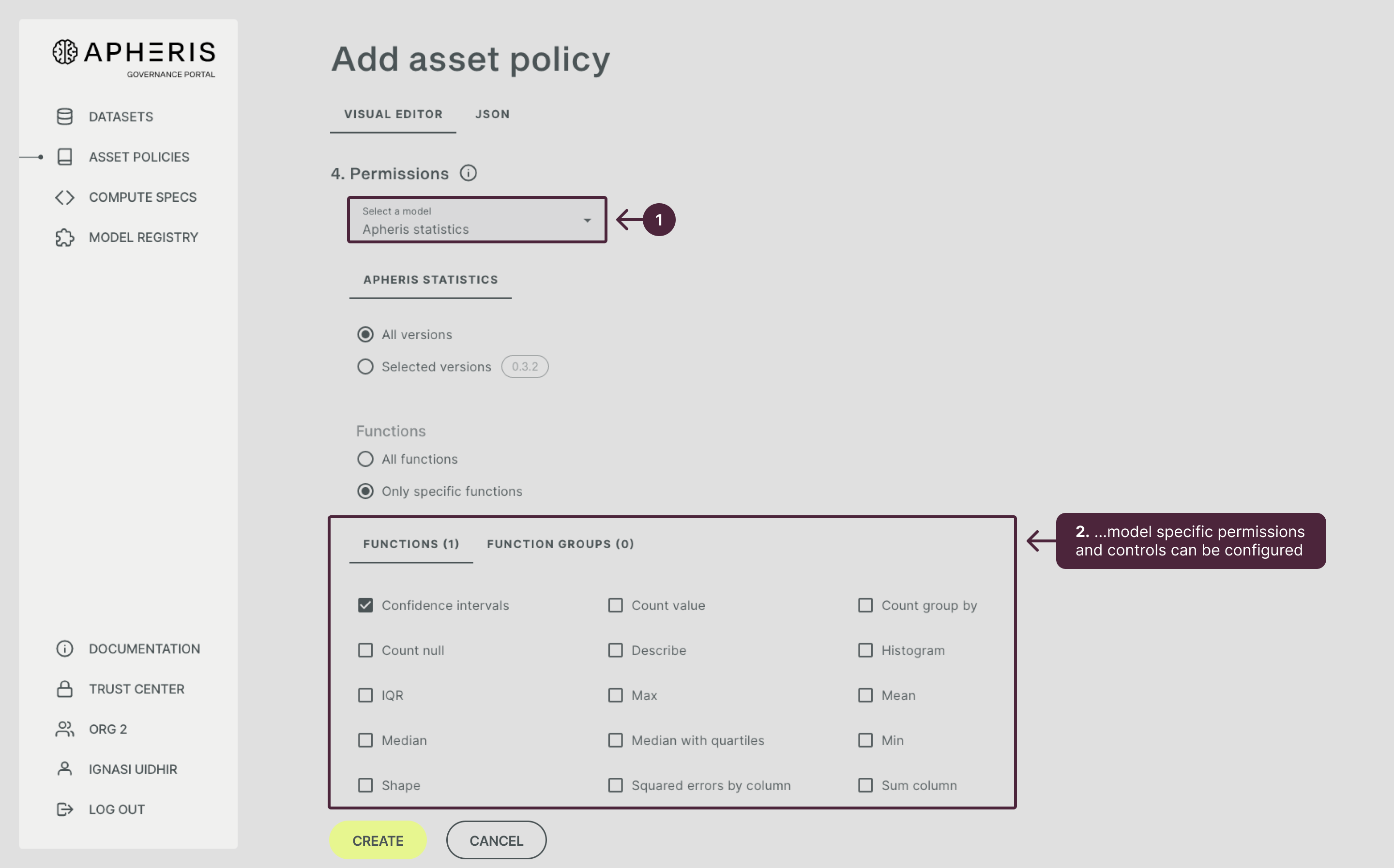
In the section “Permissions” you define the model and model version as well as the model-specific permissions that control computations on the dataset.
Each model includes model-specific controls to enable compliant computations. Therefore, after you select a model, these specific permission parameters and privacy controls for a model will appear and you can fill them in (below the permissions for Apheris Stats are shown).
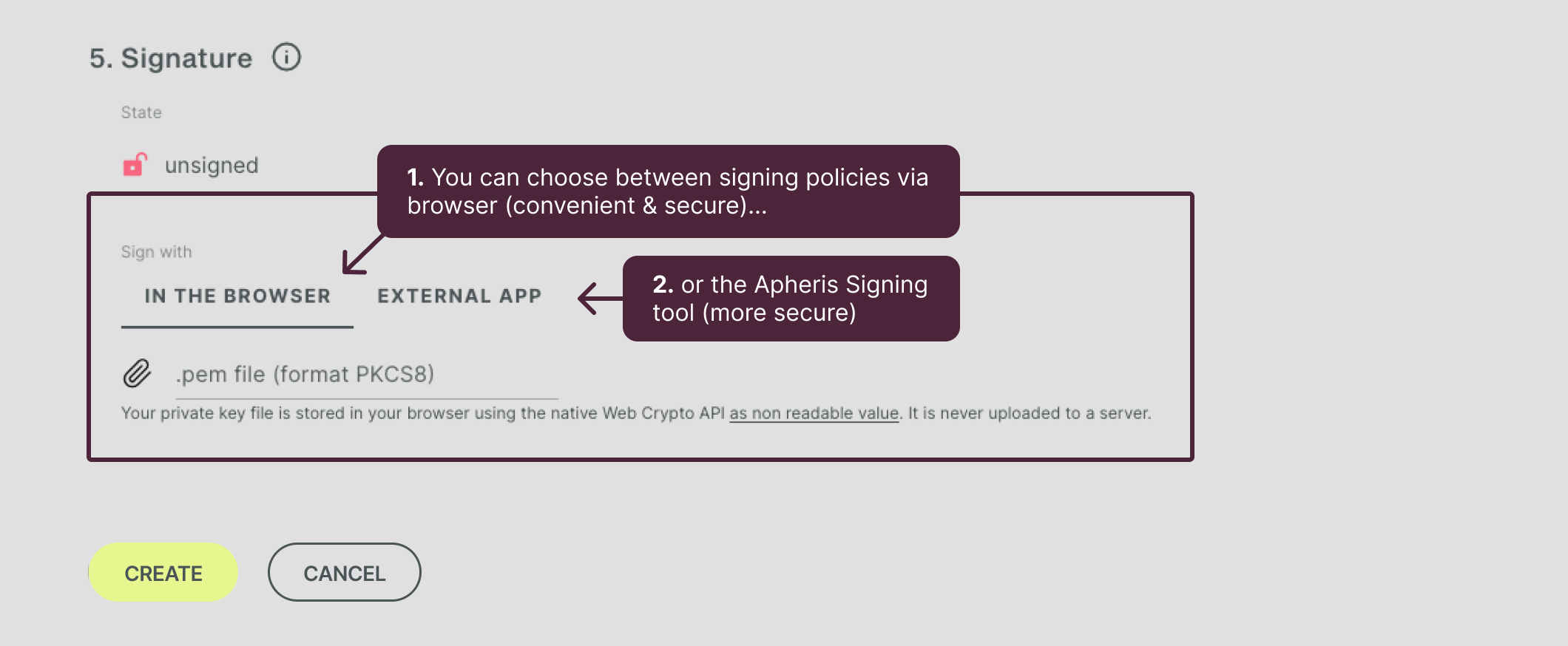
Asset Policy signing (optional)🔗
As an optional and additional security functionality, you can digitally sign the Asset Policy. This is an additional security measure to prevent tampering, as any Asset Policy that is stored on the Orchestrator and pulled from there will be verified using the digital signature before it is executed.
This requires that you as a data custodian first create an RSA key pair (you can use the Apheris signature tool for that, which an Apheris representative can provide you on request). With this key pair, you insert the public key on the Gateway at deploy time, and keep the private key with yourself. When you create a new Asset Policy, you can create a signature of that Asset Policy using your private key. The Asset Policy will then be stored together with the signature (but never your private key).
When a Compute Spec is created that involves a signed Asset Policy, the gateway will retrieve the Asset Policy, and the associated signature, and verify the signature on the gateway using the public key that is on the gateway. The computation will only be executed if the signature could be successfully verified.
You have 2 options of signing an Asset Policy:
- signing via “in the browser” (convenient, secure)
- signing via “external app” which is the Apheris signing tool (highly secure)
For a detailed step-by-step guide on signing Asset Policies and the two options, please see signing Asset Policies.
Saving the Asset Policy🔗
The next step is to save the Asset Policy by clicking ‘Save’. The Asset Policy, and the associated signature if applicable, is then stored in a database on the Orchestrator, from which the Apheris Compute Gateway will pull it when there is a Compute Spec activated on a dataset involving this Asset Policy. If the Compute Gateway is configured to verify signatures, it will take the signature that comes with the Asset Policy itself, and then verify it on the Gateway using the public key stored there before executing the computation.